System and System Line Configuration
This section provides all information which is relevant for the configuration of a System Line and a System of kind 'SAP HANA'. It can be created and administrated in the Portal's menu System Lines.
There are different types of SAP HANA connection: As of now it is possible to connect SAP HANA Tables, SAP HANA Procedure or SAP HANA SQL Statements
Prerequisites
SAP HANA ODBC Driver
Download the correct HANA ODBC Driver for the operating system the VDP Agent will be installed to. The ODBC driver is part of the SAP HANA Cloud, client utilities. Please see SAP for the latest installation instructions. The VDP Agent will need to have access to the installed driver.
Preparation for Authentication
Make yourself aware of the different SSO authentication options for ODBC connections to SAP HANA (see SAP Help).
During the setup of the authentication, we recommend to activate Database Traces for Component authentication in SAP HANA Studio (Level: INFO).
If the Component is not available, please make sure to activate the Show All Components feature.
See also SAP Help.
Configuration of a SAP System Line
The System Line configuration is equivalent to the other kinds of System Line configurations:
-
Kind: SAP_HANA
-
Authentication: Enabled
-
Short Name: A descriptive and identifying name
Configuration of a SAP HANA System
The configuration for a specific SAP HANA System is the same for all three connection types.
System data
-
Short Name: A descriptive and identifying name
-
Location: Assign the System to a Location (has to be created and enabled before)
-
Authentication (further information in the section Authentication Configuration):
- Entra ID SAML
- Entra ID OAuth2
- Shared Basic Auth (User and Password)
- Per User Basic Auth (User and Password)
- SAP Logon Ticket
After providing the System data information and saving additional information is required:
Technical parameters:
- CLIENT: Target system client, default is '000'.
- HOST_NAME: Target system base URL / hostname.
- ODBC: The port for http-connections, default is
3<instance>15. - INSTANCE: Target system instance, default is '00'.
- SYSTEM_ID: Target system ID, e. g. HDB.
- DATABASE: HANA Database name. If no database is selected, the user's default database will be connected.
- DRIVER_NAME: Name of the HANA odbc driver registered in the operating system (e.g. HDBODBC for 64-bit Windows).
- ENCRYPTED: Activate encryption for connection ('TRUE' = yes).
- CERT_VALIDATION: Toggle certificate validation ('FALSE' = no validation, default is 'TRUE').
Authentication Configuration
There are different options for the Authentication configuration.
Basic Authentication
Not recommended Basic authentication uses hard-coded database user credentials (username & password). These credentials need to be stored in Virtual Data Platform.
SAP Logon Ticket
SAP HANA allows trusted systems to generate 'SAP Logon Tickets' on behalf of a user. Virtual Data Platform can retrieve the SAP user name from your company's Entra ID. Therefore your Entra ID administrator has to configure a freely selectable property for each user. The user-specific value of this property will be used for the SAP Logon token creation and has to match the SAP user name.
To use SAP logon tickets for user authentication, you must configure SAP HANA to accept logon/assertion tickets.
Create a VDP Certificate and use it in SAP HANA
Create a certificate that is required to be
- available (including private key) on the computer's certificate store on which the VDP Agent is installed. It has to be on a computer being connected to the network your SAP system is located in.
- Imported to SAP HANA and enabled for SAP Logon Ticket verification.
For 1) please import the certificate into the certificate store of the computer the VDP Agent is running on. Make sure the system-user running the Agent is authorized to access the private key of the certificate.
For 2) Follow the instruction on SAP Help. In case of an in-database certificate collection following steps are required:
- Create a PSE and set the purpose to 'SAP LOGON' (see SAP HELP)
- Import the public part of the certificate from 1) and add it to the PSE (see SAP Help)
- Enable SAP Logon Ticket for required users
Example
CREATE PSE SAPLOGON_PSE;
SET PSE SAPLOGON_PSE PURPOSE SAP LOGON;
CREATE CERTIFICATE FROM '-----BEGIN CERTIFICATE-----MII...-----END CERTIFICATE-----'
COMMENT 'VDP SAP LOGON Certificate';
-- get the name of the uploaded certificate
SELECT CERTIFICATE_NAME FROM certificates WHERE comment = 'VDP SAP LOGON Certificate';
ALTER PSE SAPLOGON_PSE ADD CERTIFICATE <certificate name>;
ALTER USER <user name> ENABLE SAP LOGON TICKET
Entra ID SAML
If not already available, please create a SAML Identity Provider in your Azure Entra ID (e.g. SAP NetWeaver, see Microsoft Help).
SAP HANA is only validating the Entity ID and certificate of the SAML provider, thus it is not strictly required to use the 'SAP NetWeaver' Enterprise Application. The Name ID value inside the SAML Assertion will be used as external identity (more details on SAP Help).
Entra ID Configuration
If you followed the instructions you should see a corresponding entry in your app registrations (e.g. SAP NetWeaver). In Section 'Expose an API' you need to add 'VDP Global SignIn' with Client ID '1e5f54da-a828-44de-8fa7-6ecf4f6dfedf' to the 'Authorized client applications' with an authorization for the impersonation scope.
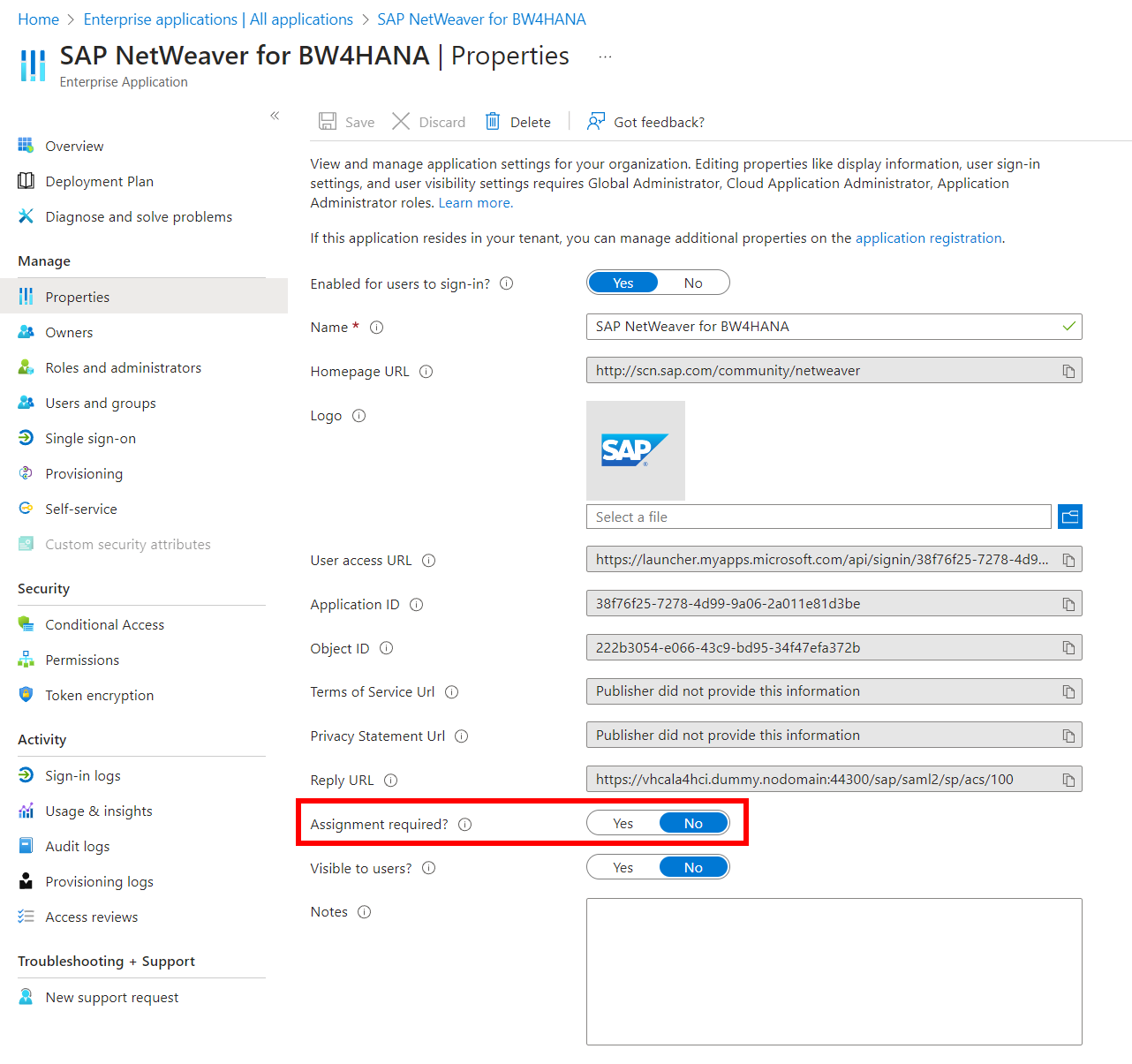
Either add all required users to your SAP NetWeaver Enterprise App Registration or go to the properties of the Enterprise App Registration and set 'Assignment required?' to 'No':
SAP HANA Configuration
Configure SAP HANA for SAML authentication (see SAP Help)
Required configuration steps:
- Create SAML Identity Provider (see SAP Help)
- Create a PSE for the Identity Provider with purpose SAML
- Import Entra ID Certificate from Enterprise Application and add it to the PSE
- Create new or use existing user to link internal and external identity
Example
CREATE SAML PROVIDER ENTRAID_SAML
WITH SUBJECT 'CN=Microsoft Azure Federated SSO Certificate'
ISSUER 'CN=Microsoft Azure Federated SSO Certificate'
ENTITY ID '<Entity ID of created Enterprise Application>' CASE INSENSITIVE IDENTITY;
CREATE PSE SAML_PSE;
SET PSE SAML_PSE PURPOSE SAML FOR PROVIDER ENTRAID_SAML;
CREATE CERTIFICATE FROM '-----BEGIN CERTIFICATE-----MII...-----END CERTIFICATE-----'
COMMENT 'SAML Certificate';
-- get the name of the uploaded certificate
SELECT CERTIFICATE_NAME FROM certificates WHERE comment = 'SAML Certificate';
ALTER PSE SAML_PSE ADD CERTIFICATE <CERTIFICATE_NAME>;
CREATE USER TEST1 WITH IDENTITY '<Value of SAML Assertion Name ID (i. e. the user id value coming from Entra ID)>' FOR SAML PROVIDER ENTRAID_SAML;
Check the VALUE of property saml_service_provider_name in your HANA configuration.
SELECT VALUE from M_INIFILE_CONTENTS WHERE FILE_NAME = 'indexserver.ini' AND LAYER_NAME = 'SYSTEM' AND KEY = 'saml_service_provider_name'
If a value is set, it must meet the Entity ID of your SAML Provider otherwise you will see an error like [SAML] Assertion is not intended for this service provider. If you leave the property empty, every Entity ID is accepted.
Change the property value in the Administration Console or via SQL:
ALTER SYSTEM ALTER CONFIGURATION ('indexserver.ini', 'SYSTEM') SET ('authentication', 'saml_service_provider_name') = ' ' WITH RECONFIGURE;
or
ALTER SYSTEM ALTER CONFIGURATION ('indexserver.ini', 'SYSTEM') SET ('authentication', 'saml_service_provider_name') = '<Entity ID>' WITH RECONFIGURE;
Entra ID OAuth2
This authentication method will use OAuth2 tokens - technically JSON Web Tokens (JWTs) - requested from Entra ID. In HANA, this is called using a JWT Identity Provider.
SAP HANA Configuration
Configure SAP HANA for JWT authentication (see SAP Help)
Required configuration steps:
- Create JWT Identity Provider (see SAP Help)
- Create a PSE for the Identity Provider with purpose JWT
- Import Entra ID Certificates and add them to the PSE
- Create new or use existing user to link internal and external Identity
Example
CREATE JWT PROVIDER ENTRAID_JWT WITH ISSUER 'https://sts.windows.net/<your Entra ID tenant ID>/'
CLAIM '<preferred JWT claim (e.g. upn)>' AS EXTERNAL IDENTITY CASE INSENSITIVE IDENTITY;
-- create all JWT certificates from https://login.microsoftonline.com/<your Entra ID tenant ID>/discovery/v2.0/keys
CREATE CERTIFICATE FROM '-----BEGIN CERTIFICATE-----MII...-----END CERTIFICATE-----'
COMMENT 'Entra ID JWT Certificate';
CREATE CERTIFICATE FROM '-----BEGIN CERTIFICATE-----MII...-----END CERTIFICATE-----'
COMMENT 'Entra ID JWT Certificate';
CREATE CERTIFICATE FROM '-----BEGIN CERTIFICATE-----MII...-----END CERTIFICATE-----'
COMMENT 'Entra ID JWT Certificate';
CREATE CERTIFICATE FROM '-----BEGIN CERTIFICATE-----MII...-----END CERTIFICATE-----'
COMMENT 'Entra ID JWT Certificate';
-- create PSE
CREATE PSE JWT_PSE;
-- get names of all previously created certificates
SELECT CERTIFICATE_NAME FROM certificates WHERE comment = 'Entra ID JWT Certificate';
-- foreach certificate
ALTER PSE JWT_PSE ADD CERTIFICATE <name1>, <name2>, <name3>, <name4>;
-- set PSE purpose
SET PSE JWT_PSE PURPOSE JWT FOR PROVIDER ENTRAID_JWT;
CREATE USER TEST1 WITH IDENTITY '<user value of selected JWT claim>' FOR JWT PROVIDER ENTRAID_JWT;