Security Concept
VDP fulfills highest security standards which key security features and principles are outlined in this section. The basic concept is to ensure data security by only accessing data directly from the Source System at the moment of user request. This design guarantees that no data is ever stored on VDP itself.
Security Principles
VDP operates under a stringent security framework aimed at minimizing data exposure and maximizing protection. The key principles include:
- Minimal Data Access: Only the minimum necessary data is accessed, and only for the shortest possible duration.
- Secure Environment: Data is processed in highly secure environments.
- Authorized Access: Access is restricted to authenticated users only.
Physical and Environmental Security
The VDP infrastructure is hosted by cloud providers certified under SOC 2 Type II and ISO 27001 standards. This certification ensures robust physical and environmental security controls, protecting data from unauthorized access and environmental threats in a multi-tenant setup.
- SOC 2 Type II Certification: Ensures controls for data protection and privacy are effectively implemented. For additional details see the Microsoft description of System and Organization Controls Type 2.
- ISO 27001 Certification: Guarantees a comprehensive Information Security Management System (ISMS) is in place to safeguard data. Again for details we refer to the official Microsoft description of the ISO 27001 certification.
Internal Security Architecture
VDP leverages a microservices architecture designed according to the Least Privilege Principle:
A security approach where each service or user is granted only the permissions needed to perform their function, reducing potential attack surfaces and damage from breaches.
This minimizes the risk of unauthorized access and lateral movement within the platform. Services authenticate each other using a Managed Identity system, and communication between services is controlled via strict network policies, preventing unauthorized interactions.
The following figure provides an overview of the technical architecture:
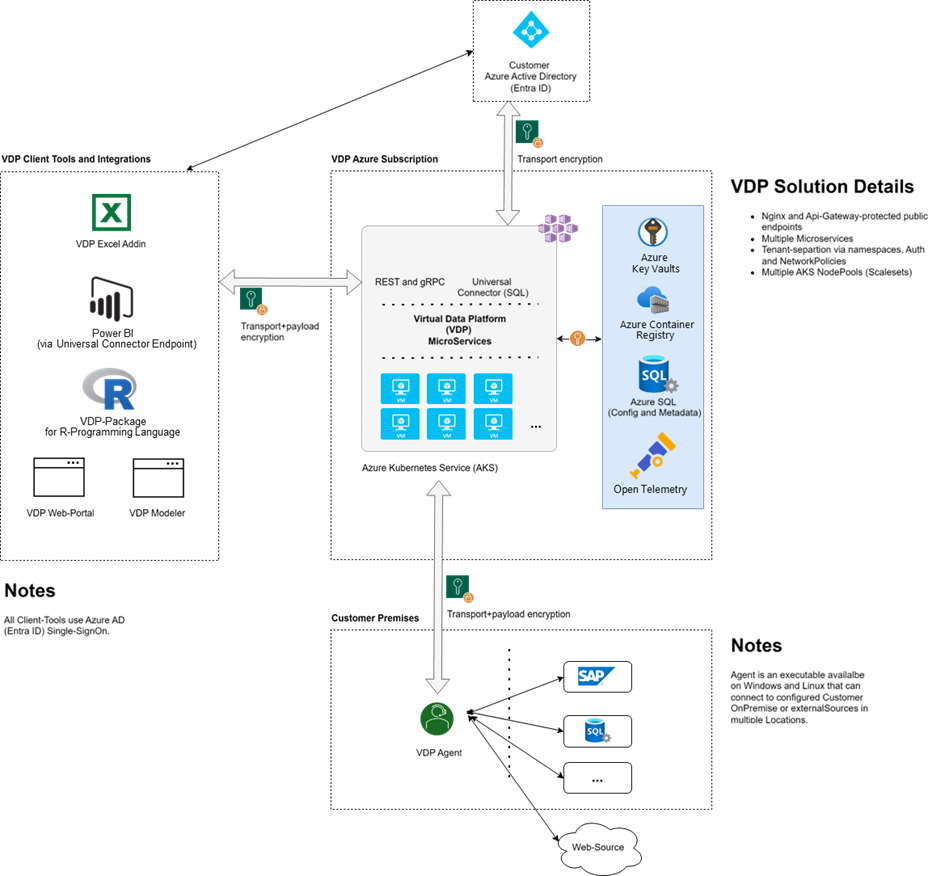
Authentication
User authentication in VDP is managed through OAuth2 at the customer's Azure Entra ID, ensuring that access control is centralized and adheres to the customer's security policies, including Multi-Factor Authentication (MFA). For Source System authentication, VDP supports Single Sign-On (SSO) technologies such as SAML, OAuth, and Logon Tokens, ensuring secure and seamless access.
User & Role Management
VDP provides a straightforward role-based access control (RBAC) system that simplifies management, configuration, and platform usage. Since VDP does not store Source System data and relies on SSO, data-level permissions are not necessary in VDP.
User Sandbox
Data from Source Systems is processed in user-specific sandboxes – temporary virtual machines activated upon user action. These sandboxes only retain data in memory and are destroyed after the user's action, ensuring data is not persistently stored or exposed.
Traffic Encryption
All data exchanges with Source Systems occur over encrypted SSL/TLS connections where supported by Source Systems. Additionally, VDP employs end-to-end-to-end encryption, securing data from the Source System to the user sandboxes and from the user sandboxes to user tools. Encryption keys are short-lived and regenerated with each new sandbox instance, preventing unauthorized data access, even within VDP infrastructure.
Sensitive Data
Any potentially sensitive configuration data is securely stored in KeyVaults, which are encrypted and inaccessible to the outside, ensuring strict confidentiality and integrity of data.
Data Protection
VDP only requires user identity details from the customer’s identity provider for license validation, without processing additional personal identifiable information (PII). If personal data from Source Systems is accessed, it is handled according to stringent security standards and removed from the platform immediately after the user's action is completed.
In summary, VDP’s security architecture and practices ensure that data remains secure, minimizing exposure and risks while providing seamless and secure data access directly from Source Systems.
Workspaces
Allows users to assign permissions for executing or editing virtual datasets within specific workspaces. It facilitates sharing configurations and managing access on datasets to enhance collaboration and security management.
Upcoming Features
VDP is continuously evolving, and we are excited to announce two new features that will further enhance user experience and data security:
-
Private Authentication: With this feature, user credentials will be stored on the platform in a user-specific, encrypted manner. This enables Single Sign-On even with legacy systems that do not support modern SSO technologies, ensuring seamless and secure access across diverse systems.
-
Authorization Layers: this planned feature will allow the definition of an authorization layer upon any data source. This is especially helpful for sources not providing any authorization features at all (e.g. legacy systems).