Technical Details and Security
Technical Details
The following section provides more details on how the Agent works conceptionally. Basically, the direction matters, who sends a requests and who or which systems answers. It is explained by using the example of a simple Google search from a user, which everyone should be familiar with:

Every user might already experienced this extensively, she or he types in a question, this is sent to a Google server and the server sents back the response. The user receives the response and can see it.

In case the direction changes, that means Google sents an unexpected request, the request is blocked by the user's firewall. No communication is possible. This is similar to: Virtual Data Platform cannot just sends request to a Source System directly.
The Agent works as follows:
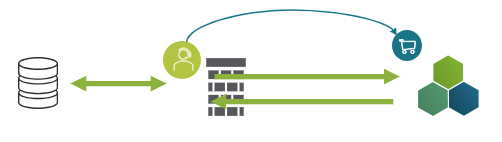
The VDP Agent controls the direction by watching to a „request-basket“. If there is a request, the agent executes it. Since the agent starts the communication, Virtual Data Platform can connect to the agent.
Security Considerations
The Agent is fulfills several security requirements. In the following are listed three important ones:
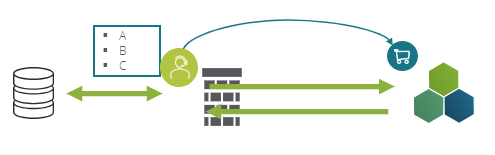
The agent is strictly limited to the predefined capabilities and supports Single-Sign-On and whitelisting for further access control.
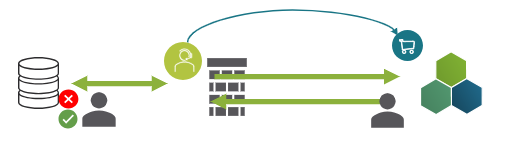
The authorization stays within the source, meaning the user‘s identity is transferred to the data source.
Full control over the agent. Without a running agent no data transfer is possible. The agent‘s operation is exclusively controlled by the network owner.